This content originally appeared on Level Up Coding - Medium and was authored by Mohit Sewak, Ph.D.
The MCP Server: The Key to Agentic AI Interoperability — But What About Security?
Discover the crucial role of MCP servers in orchestrating GenAI Agents and the potential security risks lurking beneath the surface.

Alright, fellow AI enthusiasts, buckle up! Dr. Mohit Sewak here, back from the digital trenches where GenAI agents roam free, sometimes a little too free. We’re living in an era where AI isn’t just a tool; it’s becoming a digital workforce. These “agentic workflows,” as the cool kids call them, are automating everything from booking your next vacation (hopefully somewhere with good Wi-Fi) to making complex business decisions. But what’s the unsung hero, the digital maestro conducting this symphony of silicon? Enter the Model Context Protocol (MCP) server — think of it as the USB-C port for AI, the universal translator that lets our AI agents actually do stuff with the vast ocean of data out there.
But, as with any good superhero saga, with great power comes great… well, you know the rest. While MCP servers are busy making our AI dreams a reality, they’re also potentially opening a Pandora’s Box of security nightmares. So, grab your favorite caffeinated beverage, and let’s dive into the nuts and bolts of MCP servers and why securing them is about as crucial as remembering your password (which, let’s be honest, is a daily struggle).

“The road to AI agent interoperability is paved with good intentions… and potentially a few digital landmines.” — Your Truly, Dr. Mohit Sewak
Pro Tip: Ever heard of “security by obscurity”? Yeah, doesn’t work. Especially not here. Relying on the complexity of MCP to hide vulnerabilities is like hiding your house key under the doormat… in a glass jar.
Decoding the Digital Rosetta Stone: What Exactly is an MCP Server?
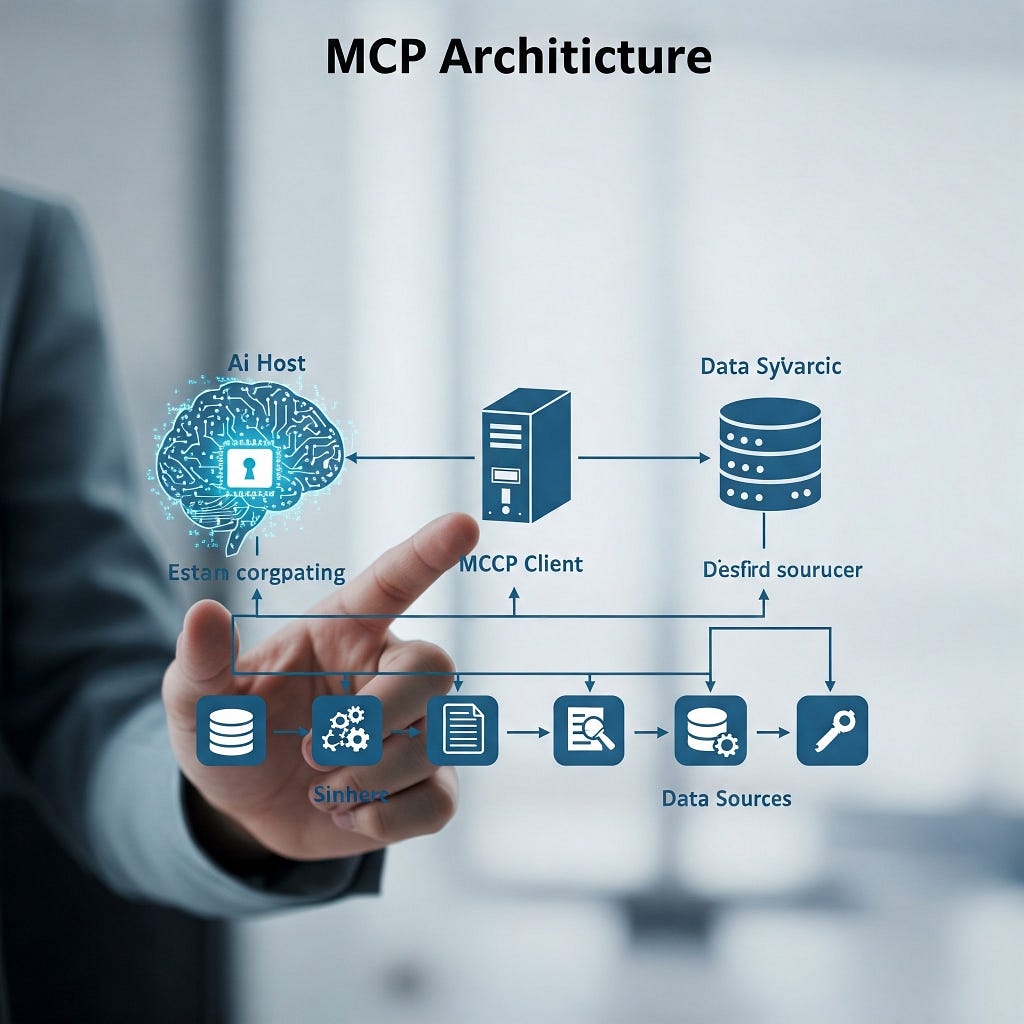
Imagine you’re trying to get a bunch of robots who speak different languages to build a car. Chaos, right? That’s where MCP comes in. The MCP standard is like a universal language and set of instructions that allows AI models (the robots) to talk to various data systems (the parts suppliers) through a well-defined architecture. This involves three main players:
- MCP Hosts: These are the brainy AI applications or agents needing data or tools. Think of them as the project managers.
- MCP Clients: The security guards, managing the one-to-one, secure connections between the hosts and the servers.
- MCP Servers: Lightweight programs exposing data sources (documents, databases, tools) through structured “primitives” like “Tools,” “Resources,” and “Prompts”. They’re the helpful librarians pointing the robots to the right shelves.
This setup lets a single AI agent tap into multiple servers, accessing a smorgasbord of data and functions. It’s like giving your Roomba the ability to also do your taxes and order groceries, all without needing a degree in electrical engineering for each integration. The beauty lies in reducing integration overhead — agents can focus on the big picture, like, say, achieving Artificial General Intelligence (AGI) or just making a really good cup of coffee. MCP also enhances decision-making by feeding agents up-to-date info, supports Retrieval-Augmented Generation (RAG) with a more structured approach, and even gives agents “memory” and “tools” for autonomous operation. Fancy, eh?
“Give me a lever long enough and a fulcrum on which to place it, and I shall move the world… Give me an MCP server, and I shall connect all the AIs.” — Dr. Mohit Sewak., inspired by Archimedes.
Trivia: MCP doesn’t just retrieve data; it enables active tool execution, unlike passive data retrieval in traditional RAG systems. It’s the difference between reading a recipe and actually having a robot chef cook the meal.
The Flip Side of the Coin: When “Universal Agency” Becomes a Universal Headache
All this interconnectedness sounds fantastic, but here’s where the plot thickens. MCP servers, by their very nature, are gatekeepers to a treasure trove of data. And guess who else likes treasure? Yep, the digital pirates, the nefarious hackers, the… well, you get the picture. Because MCP servers are fundamentally server infrastructure, they inherit a laundry list of classic server vulnerabilities:
- Unauthorized Access: Weak passwords or compromised credentials can let the bad guys waltz right in.
- Data Breaches: Once inside, they can steal or expose sensitive info, models, or anything else they fancy.
- Denial-of-Service (DoS) Attacks: Overwhelm the server, and suddenly your super-smart AI agents are as useful as a chocolate teapot.
- Malware Infections: Viruses, ransomware — the whole digital zoo can turn your server into a biohazard.
But wait, there’s more! With AI in the mix, we have a whole new layer of “fun”:
- Data Poisoning: Sneak in bad data to corrupt the AI’s learning.
- Model Inversion/Stealing: Trying to reverse-engineer or outright copy your precious AI models.
- Adversarial Examples: Crafty inputs designed to fool the AI.
- Backdoors: Hidden triggers that make the AI misbehave on command.
The interconnectedness facilitated by MCP means a breach in one server can cascade through the entire agentic workflow, like dominoes made of sensitive data and critical processes. Yikes!

“With great connectivity comes great responsibility… to patch your systems.” — Dr. Mohit Sewak, inspired by Uncle Ben.
Pro Tip: Regularly scan not just your MCP server software but also the underlying OS and all dependencies for vulnerabilities. Those “shadow vulnerabilities” in libraries can be real ninjas.
Agent Provocateurs: How MCP Servers Can Be Exploited Through the Agents Themselves
Here’s where things get particularly spicy. MCP servers don’t just serve data; they mediate the dance between agents and data sources. This means a compromised agent, or even a cleverly manipulated request from a legitimate agent, can be used to exploit the server. Imagine an agent being tricked with an “adversarial input” into divulging sensitive information or performing an unauthorized action. It’s like a ventriloquist act where the dummy starts making unauthorized bank transfers.
The autonomous nature of these agents, combined with the broad access granted by MCP, creates a juicy attack surface. Think system infiltration, privilege escalation, and data exfiltration — the hacker’s unholy trinity. Robust input validation and sanitization on the MCP server are your first line of defense, like a bouncer checking IDs at the door of your data club.

“The most dangerous flaws are the ones you don’t see coming, especially when they’re whispered by a friendly-looking agent.” — Yours Truly, Dr. Mohit Sewak.
Trivia: The principle of “least privilege” is key here. Agents should only have the access they absolutely need, minimizing the damage if they do get compromised. It’s like giving your intern access to the coffee machine but not the company bank account.
Learning from the Ghosts of Breaches Past: Control Plane Nightmares
While we don’t have specific horror stories (yet) about MCP server breaches splashed across the headlines, we can learn a lot from similar technologies. Think of cloud control planes — the dashboards and APIs that manage cloud resources. When those get compromised, bad things happen.
Remember the TeamCity vulnerability exploited by North Korean threat actors? That’s a CI/CD application, a control plane for software development, and its breach led to supply chain attack potential. Or the SolarWinds and Okta hacks? Management and support infrastructure, part of the broader control plane, were targeted. Even NASA JPL got hit because of an unauthorized device connecting to their network — a control plane failure with cosmic consequences.
The lesson? Control planes are prime targets. They offer broad access and control, making them incredibly valuable to attackers. MCP servers, acting as a control plane for AI agent interactions, fit this profile perfectly. And just like vulnerabilities in AI frameworks like PyTorch Model Server (TorchServe) can expose systems, the security of the entire software supply chain supporting your MCP server is paramount.

“Those who don’t learn from history are doomed to repeat it… and probably get pwned in the process.” — Santayana, paraphrased for the digital age.
Pro Tip: Treat your MCP server like the high-value asset it is. Apply the same level of security scrutiny you would to your most critical infrastructure.
Fort Knox for Your AI Agents: Best Practices for MCP Security
So, how do we prevent our agentic utopia from turning into a dystopian security meltdown? By building robust defenses, of course! Here’s a starter kit:
- Access Control is King (and Queen, and the Whole Royal Court): Implement Role-Based Access Control (RBAC) to ensure only authorized users and agents can access specific data and functions. Enforce the principle of least privilege — give only what’s needed, nothing more.
- MFA Everything: Multi-Factor Authentication (MFA) for all administrative access to the MCP server is non-negotiable. Ideally, extend this to agent authentication where possible.
- Encrypt All the Things: Encrypt data at rest on the server and data in transit between the server, agents, and data sources (using TLS/SSL).
- Watch Like a Hawk (or an AI Security System): Continuous monitoring of server activity and detailed logging are crucial for spotting and responding to threats. Set up alerts for suspicious activity.
- Audit Regularly: Conduct frequent security audits, vulnerability assessments, and penetration testing.
- Patch, Patch, Patch: Stay on top of security updates for your OS, MCP server software, and all dependencies.
- Segment Your Network: Isolate the MCP server to limit the blast radius if a breach occurs.
- Have a Plan for When Things Go South: Develop an incident response plan specifically for MCP server compromises.
- Validate and Sanitize: Implement strict input validation and output sanitization to guard against adversarial attacks and data leakage.

“Defense in depth is not just a catchy slogan; it’s the only way to sleep soundly when you’re managing a nexus of AI power.” — Yours Truly, Dr. Mohit Sewak.
Pro Tip: Automate your security processes where possible. Automated patching, vulnerability scanning, and even response can save precious time when under attack.
The Communication Gauntlet: Securing Agent-Server Interactions
The pathway between agents and MCP servers is a potential superhighway for attackers. We need to think about:
- Hijacked Agents: Attackers gaining control of an agent to do their bidding.
- Instruction Manipulation: Twisting an agent’s goals for malicious purposes.
- Hallucination Exploitation: Using an agent’s tendency to invent facts to cause harm.
- Data Leakage: Sensitive info slipping out during communication.
- Prompt Injection: Sneaky prompts that make the agent misbehave.
Mitigation is a multi-pronged affair: strong authentication for agents (think API keys, OAuth, or even User ID Tokens), strict input/output sanitization, TLS/SSL for encrypted chats, rate limiting to prevent abuse, and constant monitoring for weird agent behavior. We also need robust audit trails to trace any shenanigans.

“Trust, but verify — especially when it comes to the digital whispers between your agents and your data.” — Dr. Mohit Sewak, inspired by Ronald Reagan.
Pro Tip: Implement mutual authentication where both the agent and the MCP server verify each other’s identity. This adds an extra layer of trust to the communication.
Playing by the Rules: Compliance and the MCP Server
With great power comes great regulatory oversight. GenAI and MCP servers often handle data that falls under regulations like GDPR (for our European friends), CCPA (for the Californians), HIPAA (for healthcare data), and PCI DSS (for payment info). And let’s not forget the looming EU AI Act, which will put even more emphasis on risk management for AI systems.
Frameworks like the NIST AI Risk Management Framework and ISO/IEC 42001 are also becoming increasingly important. Compliance isn’t just about ticking boxes; it’s about establishing data governance, implementing security controls, ensuring transparency, and having clear accountability. Ignoring these can lead to hefty fines, reputational damage, and a whole lot of legal headaches.

“Compliance is not a limit on innovation; it’s a foundation for trust.” — Yours Truly, Dr. Mohit Sewak.
Trivia: The EU AI Act categorizes AI systems by risk, with “high-risk” applications facing the strictest requirements. Many agentic workflows powered by MCP servers could fall into this category.
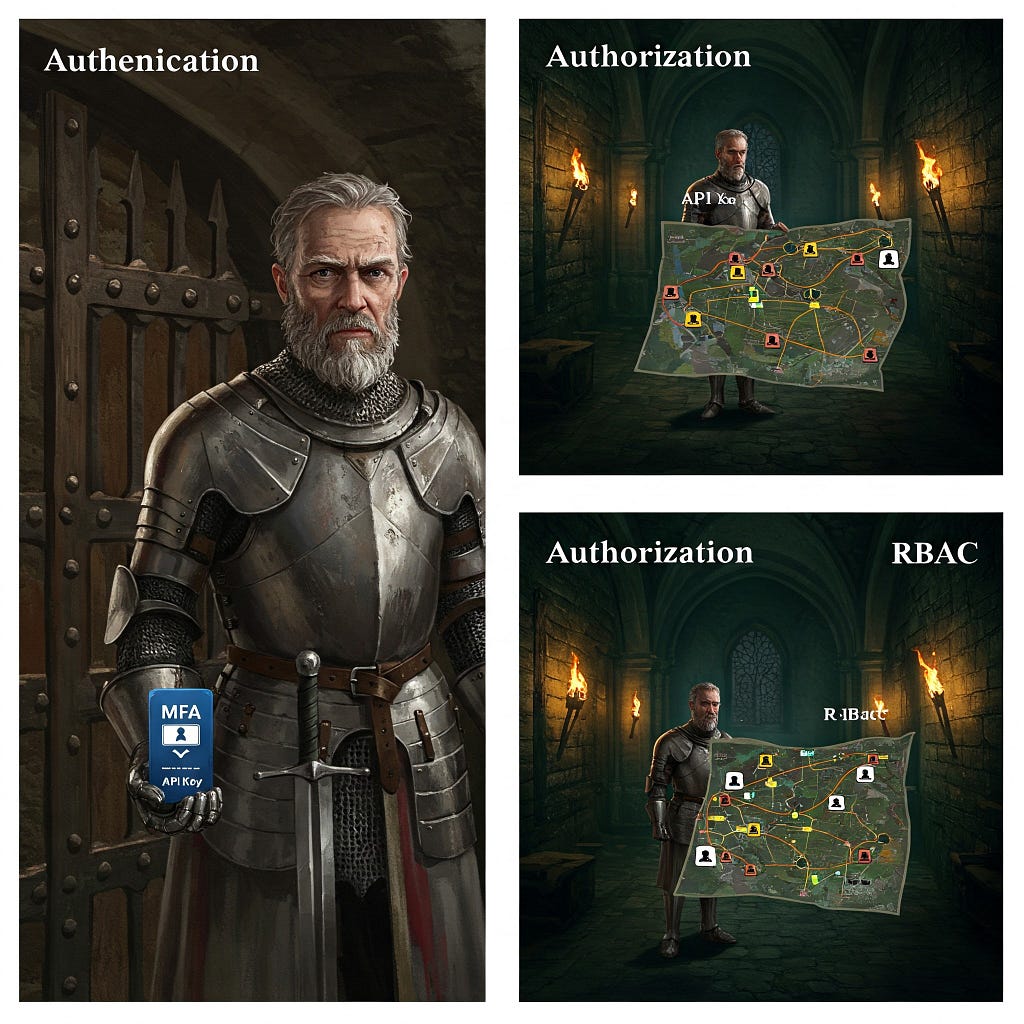
The Foundation: Authentication and Authorization — Who Goes There? And What Can They Do?
At the heart of MCP server security are two critical concepts: Authentication (are you who you say you are?) and Authorization (what are you allowed to do?).
For MCP servers, strong authentication means verifying the identity of both human admins and the AI agents connecting to it. Passwords alone are relics of a bygone era; MFA is the new standard. For agents, API tokens, OAuth, or even User ID Tokens from trusted providers are the way to go.
Authorization, guided by the principle of least privilege, dictates the “what”. RBAC is a solid approach, assigning permissions to roles and then assigning users/agents to those roles. Fine-grained permission management is crucial — down to specific API endpoints or data fields. And remember, authorization should be based on the requester’s identity, not just the output of an LLM, to avoid the dreaded “confused deputy problem”.
“Lock the door, check the lock, and then make sure only the right people have the keys to the right rooms.” — Security 101.
Pro Tip: Consider continuous authentication, where agents periodically re-verify their credentials. It’s like a regular health check for your access controls.
The Path Forward: Securing Our Agentic Future
MCP servers are a game-changer, enabling a future where AI agents can seamlessly interact with the world’s data to achieve remarkable things. But this power comes with significant security responsibilities. We can’t afford to bolt security on as an afterthought; it needs to be baked in from the ground up.
By understanding the vulnerabilities, learning from past mistakes, implementing robust best practices, and staying ahead of the regulatory curve, we can build a future where MCP servers empower innovation without compromising security or trust. It’s a challenge, yes, but one we must embrace to unlock the full potential of GenAI agentic workflows. Now, if you’ll excuse me, I have some firewall rules to update.
References
1. Overview of MCP Servers and Agentic Workflows
[1] Sewak, M. (2025). Security Issues with MCP Servers as Used in GenAl Agentic Workflows. [Unpublished manuscript].
[2] IBM. (n.d.). What is an agent? Retrieved March 23, 2025, from https://www.ibm.com/topics/agent
[3] Microsoft. (n.d.). What are Microsoft Copilot agents? Retrieved March 23, 2025, from https://learn.microsoft.com/en-us/microsoft-copilot/agents
[4] O’Reilly, T. (2024, April 11). The Model Context Protocol. O’Reilly Radar. Retrieved March 23, 2025, from https://www.oreilly.com/radar/the-model-context-protocol/
[5] Langchain. (n.d.). Agentic RAG. Retrieved March 23, 2025, from https://python.langchain.com/docs/use_cases/agentic_rag
2. Server and AI Security Vulnerabilities
[6] Cimpanu, C. (2024, February 21). North Korean hackers exploit critical TeamCity vulnerability. The Record. Retrieved March 23, 2025, from https://therecord.media/north-korean-hackers-exploit-teamcity-vulnerability
[7] Seals, T. (2024, February 29). SolarWinds Serv-U Flaw Under Active Attack. Dark Reading. Retrieved March 23, 2025, from https://www.darkreading.com/vulnerabilities-threats/solarwinds-serv-u-flaw-under-active-attack
[8] Tung, L. (2021, October 21). Okta: Hackers accessed customer support system via compromised account. ZDNet. Retrieved March 23, 2025, from https://www.zdnet.com/article/okta-hackers-accessed-customer-support-system-via-compromised-account/
[9] Goodin, D. (2019, November 15). Rogue Raspberry Pi triggered NASA JPL data breach. Ars Technica. Retrieved March 23, 2025, from https://arstechnica.com/information-technology/2019/11/rogue-raspberry-pi-triggered-nasa-jpl-data-breach/
[10] MITRE. (2024). ATLAS™ (Adversarial Threat Landscape for Artificial-Intelligence Systems). Retrieved March 23, 2025, from https://atlas.mitre.org/
[11] OWASP. (n.d.). OWASP Top 10 for Large Language Model Applications. Retrieved March 23, 2025, from https://owasp.org/www-project-top-10-for-large-language-model-applications/
[12] Narayanan, A., & Shmatikov, V. (2008). Robust De-anonymization of Large Sparse Datasets. IEEE Symposium on Security and Privacy, 111–125.
[13] Google. (n.d.). Google AI Red Team. Retrieved March 23, 2025, from https://ai.google/research/teams/ai-safety-security/responsible-ai/red-team
[14] HiddenLayer. (n.d.). HiddenLayer AI Security Platform. Retrieved March 23, 2025, from https://hiddenlayer.com/
3. Security Best Practices and Mitigation Strategies
[15] NIST. (2020). Security and Privacy Controls for Federal Information Systems and Organizations. (NIST SP 800–53 Rev. 5). National Institute of Standards and Technology.
[16] Cloud Security Alliance. (2023). Security Guidance for Critical Areas of Focus in Cloud Computing v4.0.
[17] Open Worldwide Application Security Project. (n.d.). OWASP Top 10. Retrieved March 23, 2025, from https://owasp.org/www-project-top-10/
[18] Center for Internet Security. (n.d.). CIS Controls. Retrieved March 23, 2025, from https://www.cisecurity.org/controls/
[19] Threat Intelligence. (n.d.). Securing AI Agent Authentication: Risks & Best Practices. Retrieved March 23, 2025, from https://www.threatintelligence.com/blog/ai-agentware1
[20] Qwiet AI. (n.d.). AppSec 101 — Authentication and Authorization.2 Retrieved March 23, 2025, from https://qwiet.ai/appsec-101-authentication-and-authorization/
4. Compliance and Regulatory Frameworks
[21] European Parliament. (2023). Proposal for a Regulation laying down harmonised rules on artificial intelligence (Artificial Intelligence Act).
[22] NIST. (2023). Artificial Intelligence Risk Management Framework (AI RMF 1.0). National Institute of Standards and Technology.
[23] ISO. (2023). ISO/IEC 42001:2023 Information technology — Artificial intelligence — Management system. International Organization for Standardization.
[24] Tevora. (n.d.). What is AI Compliance and Why It Matters For Businesses. Retrieved March 23, 2025, from https://www.tevora.com/resource/what-is-ai-compliance/
[25] InterVision Systems. (n.d.). Enhancing AI Security and Compliance. Retrieved March 23, 2025, from https://intervision.com/blog-enhancing-ai-security-and-compliance/
Disclaimers and Disclosures
This article combines the theoretical insights of leading researchers with practical examples, and offers my opinionated exploration of AI’s ethical dilemmas, and may not represent the views or claims of my present or past organizations and their products or my other associations.
Use of AI Assistance: In the preparation for this article, AI assistance has been used for generating/ refining the images, and for styling/ linguistic enhancements of parts of content.
License: This work is licensed under a CC BY-NC-ND 4.0 license.
Attribution Example: “This content is based on ‘[Title of Article/ Blog/ Post]’ by Dr. Mohit Sewak, [Link to Article/ Blog/ Post], licensed under CC BY-NC-ND 4.0.”
Follow me on: | Medium | LinkedIn | SubStack | X | YouTube |
The MCP Server: The Key to Agentic AI Interoperability — But What About Security? was originally published in Level Up Coding on Medium, where people are continuing the conversation by highlighting and responding to this story.
This content originally appeared on Level Up Coding - Medium and was authored by Mohit Sewak, Ph.D.
Mohit Sewak, Ph.D. | Sciencx (2025-04-03T19:44:44+00:00) The MCP Server: The Key to Agentic AI Interoperability — But What About Security?. Retrieved from https://www.scien.cx/2025/04/03/the-mcp-server-the-key-to-agentic-ai-interoperability-but-what-about-security/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
