This content originally appeared on DEV Community and was authored by Jose Luis Sastoque Rey
In this post we are going to see the AWS networking foundations, networks, subnetworks, firewall, Internet Gateway, Access Control List, NAT and others services.
Building networks, segregate the network, configure routing and network permissions are architectural decisions important to communications between the systems. Compute Services (EC2, ECS, EKS), Data Base (RDS, Aurora, ElastiCache) and more, allow us to choose the network, subnetwork, availability zone and firewall for deployment and execution the AWS service. It is our responsibility set up the communications needed for the systems and protect them against security attacks that impact availability and integrity.
We start from inwards to towards with the services that are base to other services. Each service has a description, scope, limits and an example to know their capabilities and boundaries. Let's starts.
Virtual Private Cloud (VPC)
Type: Networking
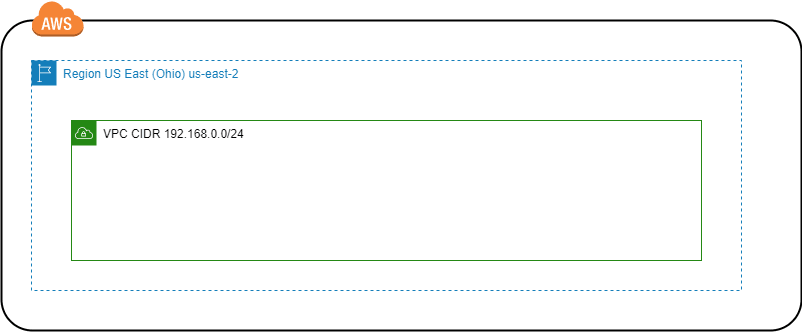
Scope: Create virtual private network with IP addresses block (CIDR). It allows isolate logically the resources deployed in the virtual network from other services that are in AWS cloud.
Limits: 5 VPC per AWS region. You can adjust the limit by requesting it to AWS support.
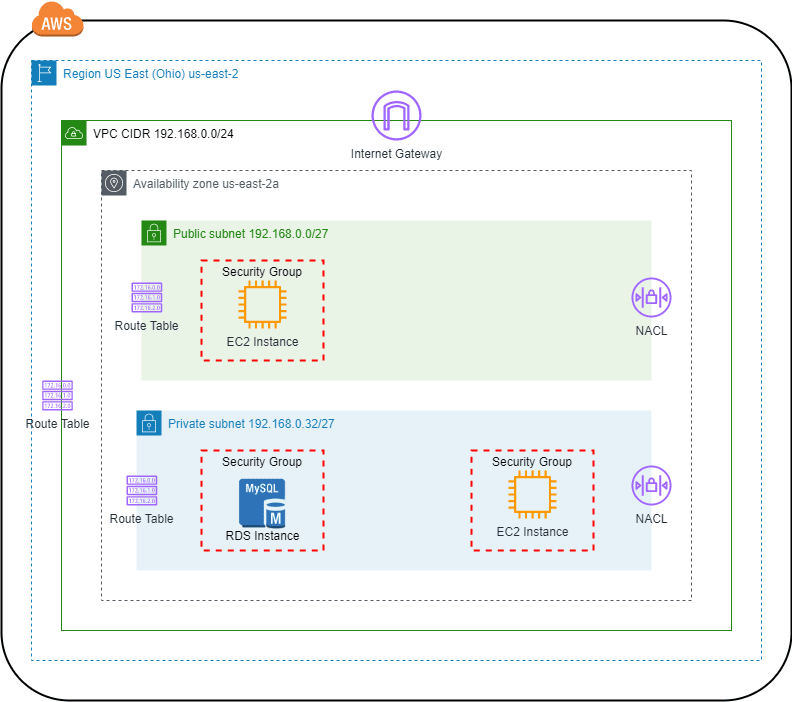
Example: To create a VPC you need IPv4 CIDR block or IPv6, this value depends of the number of subnetworks and hosts you need. We use CIDR block 192.168.0.0/24 to create VPC on Ohio AWS region. When you create a VPC by default create Route Table and Network Access Control List (NACL).
Subnets
Type: Networking
Scope: Create virtual subnetwork inside VPC network to split the network and allow deploy systems on subnetwork. You can choose the availability zone (AZ) of AWS region to create the subnetwork and you can create more than one subnetwork in the same AZ.
Limits: 200 subnets per VPC. You can adjust the limit by requesting it to AWS support.
Example: To create a VPC you need IPv4 CIDR block that is inside IPv4 CIDR block of VPC.
Taken 3 bits of VPC network address then we can create 8 subnets (2^3=8). The IPv4 CIDR block for each subnet are:
- 192.168.0.0/27
- 192.168.0.32/27
- 192.168.0.64/27
- 192.168.0.96/27
- 192.168.0.128/27
- 192.168.0.160/27
- 192.168.0.192/27
The other 5 bits are to create hosts, the number of hosts per subnet is 27 (2^5 = 32 - 5). AWS reserve 5 ip addresses in each subnet, the first 4 addresses and the last one.
For the 192.168.0.0/27 CIDR block the ip addresses reserve by AWS are:
- 192.168.0.0, Subnetwork address.
- 192.168.0.1, reserve by AWS for VPC Router.
- 192.168.0.2, reserve by AWS for Amazon provided DNS.
- 192.168.0.3, reserve by AWS for future use.
- 192.168.0.31, Broadcast, AWS does not support Broadcast communication inside VPC.
For the 192.168.0.32/27 CIDR block the ip addresses reserve by AWS are:
- 192.168.0.32, Subnetwork address.
- 192.168.0.33, reserve by AWS for VPC Router.
- 192.168.0.34, reserve by AWS for Amazon provided DNS.
- 192.168.0.35, reserve by AWS for future use.
- 192.168.0.63, Broadcast, AWS does not support Broadcast communication inside VPC.
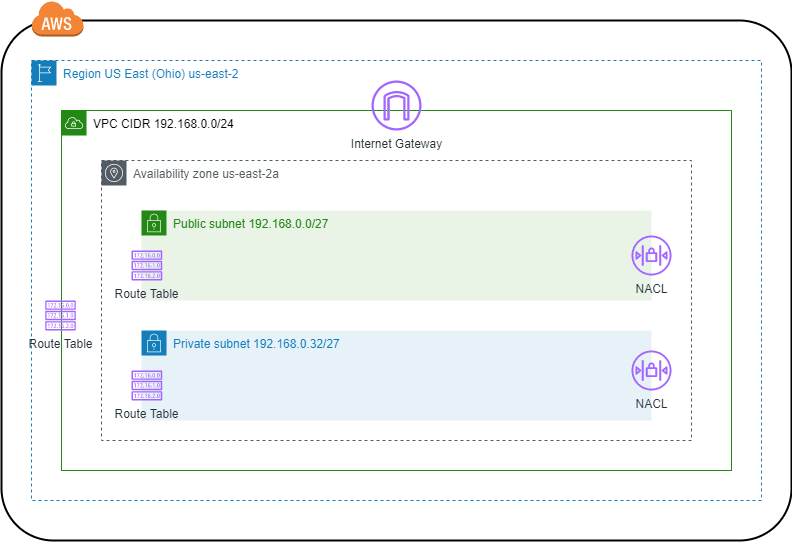
We are going to use the 192.168.0.0/27 CIDR block for Public Subnet (Internet access) and 192.168.0.32/27 CIDR block for Private Subnet (Internal access) on availability zone us-east-2a.
Internet Gateway
Type: Networking
Scope: Internet access gateway for the resources deployed in subnet and VPC. Also, it is a NAT for instances (EC2, RDS) that has public ip address.
Limits: 5 Internet Gateway per AWS Region. You can adjust the limit by requesting it to AWS support.
Example: Create Internet Gateway for the VPC 192.168.0.0/24. Just can attach one Internet Gateway per VPC.
Route Table
Type: Networking
Scope: Create routing rules to address the communications from the resource inside subnet and VPC to destination. Route Table attach to VPC applies to all subnets of the VPC. Route Table attach directly to subnet has priority over Route Table of VPC.
Limits: 200 Route Tables per VPC and 50 routing rules by Route Table. You can adjust the limit by requesting it to AWS support.
Example: Create and attach new Route Table on Public Subnet (192.168.0.0/27) with routing rules to Internet and local network:
For Private Subnet (192.168.0.32/27) create new Route Table and attach to it with routing rule to local network:
Network Access Control List (NACL)
Type: Security
Scope: Network firewall to control inbound and outbound communication to resources deployed in subnet using rules. The rule specifies communication protocol, port, source/destination and allow or deny communication. The rules are sort by number, have precedence and are stateless, you need create inbound and outbound rules to requests and responses.
Limits: 200 NACL per VPC and 20 rules to IPv4 or IPV6 per NACL. You can adjust the limit by requesting it to AWS support.
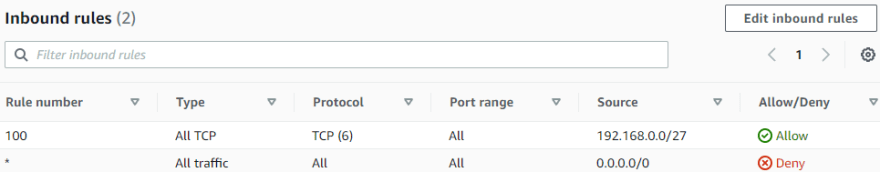
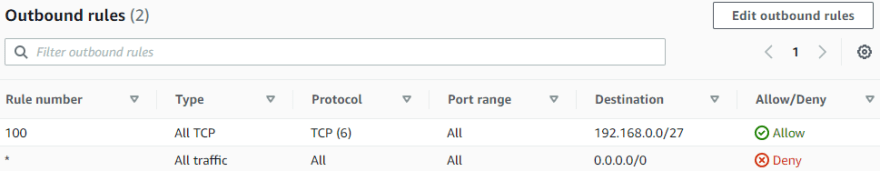
Example: For Public Subnet (192.168.0.0/27) create and attach NACL with inbound and outbound rules to allow internet access (all communications).
For Private Subnet (192.168.0.32/27) create and attach NACL with inbound and outbound rules to allow communications from and to Public Subnet (192.168.0.0/27).
Security Group
Type: Security
Scope: Instance firewall to control inbound and outbound communication to instances (EC2, RDS) using rules. The rule specifies communication protocol, port and source/destination. The rules are stateful you just need to create inbound rules to incoming request and is not necessary create outbound rules to response.
Limits: 2500 Security Group per AWS Region and 60 inbound and outbound rules per Security Group. You can adjust the limit by requesting it to AWS support.
Example: For EC2 instance access over internet using HTTP and SSH protocols, deploy on Public Subnet (192.168.0.0/27), create and attach Security Group with inbound rules with sources anywhere and ip address (your ip).
For EC2 instance to internal access only (not internet access) deploy on Private Subnet (192.168.0.32/27), create and attach Security Group with inbound rule that allow communication from Security Group EC2 Instance of Public Subnet (192.168.0.0/27) over TCP protocol and port 22.
For RDS instance to internal access only (not Internet access), deploy on Private Subnet (192.168.0.32/27), create and attach Security Group with inbound rule that allow communication from Security Group EC2 Instance of Public Subnet (192.168.0.0/27) and Security Group EC2 Instance of Private Subnet (192.168.0.32/27), both of them over TCP protocol and port 3306.
NAT Instance & NAT Gateway
Type: Networking
Scope: Internet access to instances on Private Subnets (without Internet Access) through exchange of ip addresses. Taken the ip address of communication packages send by instances and replace it with the ip address of NAT.
NAT Instance: It is EC2 instances with preconfigured Amazon Machine Image (AMI) and elastic ip address or public ip. The bandwidth depends on the bandwidth of the instance type.
NAT Gateway: Is a NAT service managed by AWS with high availability and elastic ip. Scale up to 45 Gbps in bandwidth. It can handle communication to internet, between VPCs and between VPC and on-premise corporate network.
Limits NAT Instance: Apply EC2 limits.
Limits NAT Gateway: 5 NAT Gateway per availability zone of AWS region. You can adjust the limit by requesting it to AWS support.
Example:
NAT Instance: Create EC2 instance with NAT AMI and deploy on Public Subnet (192.168.0.0/27) with internet access through Internet Gateway. On Route Table of Private Subnet (192.168.0.32/27) add routing rule to NAT instance when destination is internet.
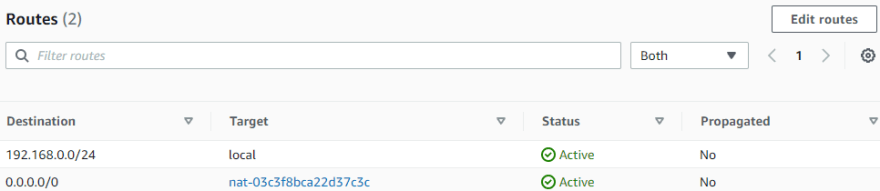
NAT Gateway: Create NAT Gateway and deploy on Public Subnet (192.168.0.0/27) with internet access through Internet Gateway. On Route Table of Private Subnet (192.168.0.32/27) add routing rule to NAT Gateway when destination is internet.
Update NACL of Private Subnet (192.168.0.32/27) with inbound and outbound rules that allow internet communications.
Route Table and NACL of Public Subnet (192.168.0.0/27) without changes.
References
This content originally appeared on DEV Community and was authored by Jose Luis Sastoque Rey
Jose Luis Sastoque Rey | Sciencx (2021-10-12T03:58:41+00:00) AWS Networking from scratch. Retrieved from https://www.scien.cx/2021/10/12/aws-networking-from-scratch/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.