This content originally appeared on DEV Community and was authored by Anshuman Abhishek
Let' Start
What is Dev-Sec-Ops?
DevSecOps stands for development, security, and operations. It's an approach to culture, automation, and platform design that integrates security as a shared responsibility throughout the entire IT lifecycle.
It is a endless field. Here we only focus about Infra and DevOps level security. We will discuss on both OSS and Paid tools which we can implement on CICD pipeline to make secure.
What is CIS?
- The Centre for Internet Security (CIS) provides a standardized set of security benchmarks to identify and refine effective security measures for specific set of tools and technologies.
- It provides security benchmark and the National Checklist Program (NCP), defined by the NIST
- They offer guidance on the security configurations of the operating system, clouds, database, virtualization, framework, and application
- In addition to the benchmark documents, the CIS also provides downloadable tools for secure configuration scanning cisecurity.org/cis-benchmarks/
- Best practice is to implement multiple scanning tool instead of trust on one.
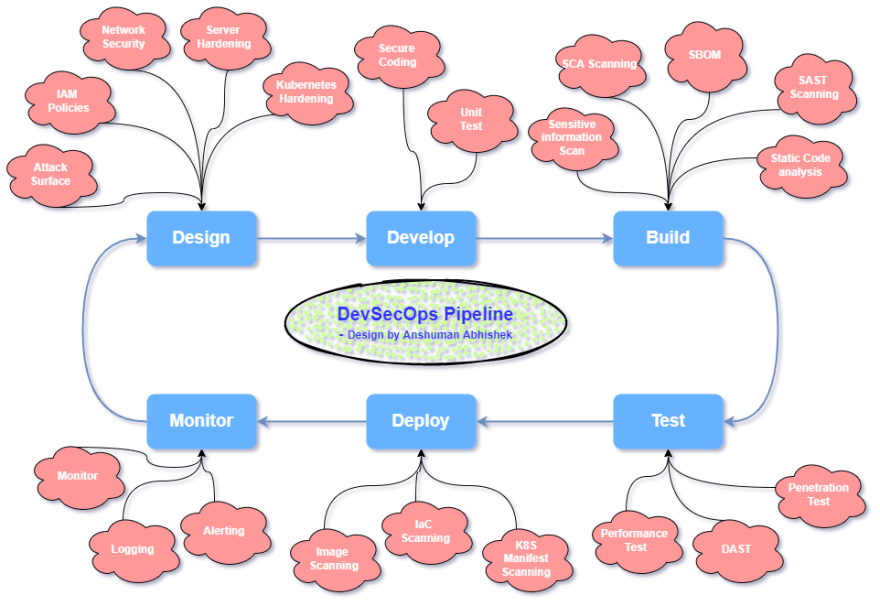
How DevSecOps pipeline looks like?
We will cover how to implement these:
- Design
- Develop
- Build
- Test
- Deploy
- Monitor
Design
Security and monitoring is always a second step, 1st step is to harden your infrastructure.
More than 80% attacks happens because of misconfiguration
In AWS, you can check how much percentage your server follow the CIS benchmark. But also keep in mind CIS =! Enough
You should not rely only on CIS and always follow best security practices
When you create a server in AWS with just port 22 open. You notice that there will be multiple attempt start happening. It will reach to 100-1000 within 1 week.
Check the vulnerability vectors you have in your system/environment where attacker can push their code or extract data.
Attack Surface
- The attack surface of a system is the collection of points(attack vectors) where unauthorized user (attacker) may enter to inject data to or extract data from an environment
- Keeping the attack surface as small as possible is a basic security measure
- Ex - Use bastion server and put all the servers in private subnet
IAM
- Identity and Access Management (IAM) is the process of granting or restricting access to computing resources for individual users, groups, or systems.
- IAM - Authentication, Authorization, User Management, and Credentials Repository
- Best practice is to Fine-Grained IAM Roles for Service Accounts and Users
Network Security
- Implement private subnets. Deploy your VMs with only private IPs. Provide secure outbound internet connections with Cloud NAT
- Turn on real-time monitoring, logging, and alerting
- Best practice is to only implement public faced LB. Also enable services like web-application firewall (WAF) and DDoS mitigation service like cloud armor.
- Fine grained networking policy on servers, resources and VPCs. Only open required IP range and ports.
Server Hardening
- It is a practice of enhancing each server's security. Even though we use the containers for deployment we have to make sure the underlying infrastructure is also secure.
- Team can consult benchmark from CIS and application such as OpenSCAP to review possible server vulnerabilities and determine what steps to take to mitigate risks
- A server must be hardened before the applications and tooling hosted on the server like Kubernetes worker server can be secured
- Implement App Armor Profile and Sec Comp Profile
- You can use Ansible playbook devsec.hardening to harden linux OS, mysql, nginx and ssh here is the link dev-sec / ansible-collection-hardening
Kubernetes
- I assume that you are using service based Kubernetes cluster and only managing worker server. If you are managing master node then use kube-bench. It is a tool that checks whether Kubernetes is deployed securely by running the checks documented in the CIS Kubernetes Benchmark.
- Only use harden image for worker server. All cloud provider provide CIS benchmark harden image.
- Secrets - Use them but make sure they're encrypted and have RBAC applied
- Security Context - Much of the Runtime practices mentioned can be enforced via SC
- Network Policy - Start with zero-trust(block every thing by default) and add allow rules only as necessary. Best practice to use Service Mesh(like Linkerd or Istio) which provide a lot of feature. If you don't want to implement service mesh then at least use calico overlay network instead of flannel because it support strong network policy management and access control list (ACLs). -- By default, pods accept traffic from any source. The network policy resource in k8s provides a means of configuring whether connections are accepted or refused. You can configure inbound and outbound rules by port, direction, protocol, and other attributes.
- Enforcement - Use OPA(Gatekeeper), Kyverno, etc to apply policies like 'each namespace should have tag of service mesh'.
Develop
- Use IDE like VSCode where you can implement plugins.
- Use SonarLint's free and Open Source VS Code IDE extension. Perform static analysis on JavaScript, Java and Python code.
- Don't hardcode credentials and sensitive information in code instead use environment variable. Also when you use env variable give space at first to not record in history. Ex - $ export CRE=abcd
- Use branching and PR request methods.
Build
Sensitive Information Scanning
- Detecting and preventing hardcoded secrets like passwords, api keys, and tokens in git repos.
- Attackers keep scanning git repo for keys/secrets. If you by mistake upload keys in repo then automatic hacker tool start building VMs on cloud platform and use for mining. Now even cloud providers are smart enough and they also run tools to grep these sensitive information. If they find then immediately send you mail with all information.
- OSS - Gitleaks and truffleHog
docker pull zricethezav/gitleaks:latest
docker run -v ${path_to_host_folder_to_scan}:/path zricethezav/gitleaks:latest [COMMAND] --source="/path" [OPTIONS]
SCA scanning
- SCA stands for the Source Composition Analysis. Scanning the dependency (eg library) used in the application for security vulnerabilities
- In any application code is just 10% and rest is Open Source Code which has ton of lines of codes which you have not written
- OSS for python is pyraider
pip install pyraider
pyraider check -f /Users/raider/project/requirements.txt -e json result.json -e html result.html
pyraider check -f /Users/raider/project/Pipfile.lock
SAST Scanning
- SAST stands for Static Application Security Testing. It is the methodology for finding the security flaws in the application from the source code. It is White-box Security testing methodology.
- There are tons of tools available. You can refer this OWASP. Try to implement tool which follow CIS benchmark.
- OSS for python is bandit
pip3 install bandit
bandit -r path/to/your/code
Static Code Analysis
- It is Code Quality and Code Security scan. It empowers all developers to write cleaner and safer code.
- The only tools I know till now for this purpose is SonarQube that is an open-source platform for continuous inspection of code quality to perform automatic reviews with static analysis of code to detect bugs, code smells, and security vulnerabilities on 20+ programming languages.
- Best practice is to enable gating with 80% code coverage.
docker run \
--rm \
-e SONAR_HOST_URL="http://${SONARQUBE_URL}" \
-e SONAR_LOGIN="myAuthenticationToken" \
-v "${YOUR_REPO}:/usr/src" \
sonarsource/sonar-scanner-cli
SBOM
- Modern software is assembled using third-party and open source components. They are glued together in complex and unique ways and integrated with original code to achieve the desired functionality. An accurate inventory of all components enables organizations to identify risk, allows for greater transparency, and enables rapid impact analysis.
- OSS for SBOM is CycloneDX. It is a lightweight software bill of materials (SBOM) standard designed for use in application security contexts and supply chain component analysis.
pip install cyclonedx-bom
pip freeze > requirements.txt
cyclonedx-bom -r -i PATH/TO/requirements.txt -o sbom.xml
Test
DAST
- DAST stands for dynamic application security testing. It is the methodology for finding the security flaws in the application when running. It is Black-box Security testing methodology
- For DAST we need to implement test environment and after test complete destroy the environment to reduce cost. Best way to provision infrastructure for test environment is by using terraform.
- OSS for DAST testing is ZAP
zap.sh -daemon -host some-host -port some-port -config api.addrs.addr.regex=true -config api.disablekey=true
Performance Test
- It is a practice of evaluating how a system performs in terms of responsiveness and stability under a particular workload. Performance tests are typically executed to examine speed, robustness, reliability, and application size. The process incorporates “performance” indicators such as:
- It gathers all the tests that verify an application’s speed, robustness, reliability, and correct sizing. It examines several indicators such as a browser, page and network response times, server query processing time, number of acceptable concurrent users architected, CPU memory consumption, and number/type of errors which may be encountered when using an application.
- OSS tool is JMeter. It is one of popular open-source tool in the performance space to help measure load time.
jmeter -n -t test.jmx -l testresult.jtl
Penetration Test
- Penetration tests (pentests)are a form of DAST (blackbox) that use external program to interrogate applications through their exposed API and HTTP endpoints.
- Penetration tests simulate automated cyber attacks on production infrastructure.
- It detect common vulnerabilities such as injection, cross-site scripting and flaws in authentication and identity and access management(IAM)
- OSS for Pentest is Arachni. It is a feature-full, modular, high-performance Ruby framework aimed towards helping penetration testers and administrators evaluate the security of web applications.
arachni $URL --report-save-path=$ {BUILD_TAG}.afr
arachni_reporter ${BUILD_TAG}.afr --reporter=html:outfile=${BUILD_TAG}.zip
unzip ${BUILD_TAG}.zip
rm -f ${BUILD_TAG}.zip
publish html report
Deploy
IaC Scanning
- Scan cloud infrastructure configurations to find misconfigurations before they're deployed. It also scan security vulnerability in cloud infrastructure like IAM user has admin role.
- There are multiple of OSS available. Few of them are terrascan, tfsec and Checkov
terraform init
terraform plan -out tf.plan
terraform show -json tf.plan > tf.json
checkov -f tf.json
K8S Manifest Scanning
- Most of the scanner which scans IaC code are capable to scan kubernetes manifest files.
- It scan misconfigurations and security vulnerability in Kubernetes (JSON/YAML), Helm v3, and Kustomize.
- It scan manifest files for runAsNonRootCheck, privilegeEscalationCheck, readOnlyFileSystem, imageVersionnotusinglatest, securityContextUsed and many more.
- OSS are Terrascan, KubeLinter and Checkov
checkov -f deployment.yml -f service.yml
Image Scanning
- Scan for vulnerabilities in container images, file systems, and Git repositories, as well as for configuration issues.
- Historically, developers have owned the security posture of their own code and the libraries used. Containers add security concerns at the operating-system level such as base-image selection, package installation, user and file permission, and more.
- Don't run as root - Yor probably don't need it.
- Privileged Containers - You almost definitely don't need it.
- Drop capabilities - Most apps don't need even Linux capabilities; dropping all and allow only what's needed. Most of the people consider alpine as a base image.
- Read Only Root Filesystem - Immutability makes exploiting your container harder.
- Deploy from known sources - Pull from known registries only
- OSS are trivy and Twistlock
trivy image python:3.4-alpine
Monitoring
- It has combination monitoring, logging and alerting.
- Monitor resources, logging application outputs and alerting events like uptime checks.
- There are multiple stacks available one of them is EFK - Elasticsearch, Fluentd, and Kibana. They are resource consuming stack.
- One of best stack in this field is Prometheus, Grafana and Loki.
- In ISTIO service mesh, Jaeger and Kiali are available.
- Few paid services in this field which are known to be best in monitoring Kubernetes pods and services are New Relic, Dynatrace, Sysdig and Datadoghq.
Recap:
OSS tools mentioned:
- kube-bench - Kubernetes Hardening
- ansible-collection-hardening - Linux Hardening
- Linkerd or Istio - Service Mesh
- OPA(gatekeeper) and Kyverno - Policy
- Gitleaks and Trufflehog - Sensetive Information
- pyraider - Source Composition Analysis
- bandit - SAST
- SonarLint and SonarQube - Static Code Analysis
- Cyclonedx - SBOM
- ZAP - DAST
- Jmeter - Performance Test
- Arachni - Pentration Test
- Terrascan, Tfsec, KubeLinter and Checkov - IaC and k8S
- Trivy and Twistlock- Image Scanning
- Prometheus, Grafana and Loki - Monitoring
- Elasticsearch, Fluentd, and Kibana - Monitoring
Paid Tools which need to consider if you and your manager are more concerned about security:
- Snyk - OpenSource, Code, Container and IaC Scan
- Fortify - Static Code Analyzer
- Codacy - Measure code quality
- New Relic
- Dynatrace
- Sysdig
- Datadoghq
Final Notes:
Almost all the scanning tools mentioned above can be implemented on any CICD pipeline like GitHub Action, GilabCI, CircleCI, Jenkins, Tekton, or any pipeline which support container based integration in it. I have tried to show examples of cli commands through which it scan. Almost all OSS scanning tools has docker image also on Dockerhub registry through that you can easily pull and run scan test. You need to implement checks after every scan and if it get failed then send reports to the person who trigger the pipeline.
This content originally appeared on DEV Community and was authored by Anshuman Abhishek
Anshuman Abhishek | Sciencx (2021-12-24T22:05:05+00:00) DevSecOps: Implement security on CICD Pipeline. Retrieved from https://www.scien.cx/2021/12/24/devsecops-implement-security-on-cicd-pipeline/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.